These days, phishing is a widely discussed topic, especially during October, which is Cybersecurity Awareness Month. There are plenty of examples of companies being hacked using this technique, and the breach of 40 million credit card numbers at Target, for instance, started with a phishing attack.

On a Saturday night, a security engineer at Equifax was updating an SSL certificate on a Network Intrusion Detection System (NIDS). Immediately after, suspicious connections were detected. After a more in-depth investigation, it became evident that the situation was far graver than anticipated. A se...

The AES algorithm is widely used today, whether it’s for encrypting a connection to a website, encrypting data on your hard drive, or storing passwords in your favorite password manager. It has been battle-tested for many decades and is still recommended as one of the most secure algorithms. In this...
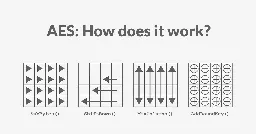
In this article, I explain how AES encryption works and how the algorithm is implemented.
There are several modded Discord clients available that allow you to tweak the appearance or add certain features. However, some plugins can even unlock certain functionalities that require a paid subscription to Discord Nitro. How is this possible?

Have you ever tried to download videos from YouTube? I mean manually without relying on software like youtube-dl, yt-dlp or one of “these” websites. It’s much more complicated than you might think.

It was quite nostalgic to do the research while writing this article!
This is the story and the technical details of how the hacker group named Fail0verflow (formerly known as Team Twiizer) discovered and exploited numerous vulnerabilities to defeat the security mechanisms of the Nintendo Wii.

You are describing TLS, which is commonly used for websites and web apps.
Try the following command:
openssl s_client -connect infosec.pub:443
The public key, the authority that signed the certificate, and the cypher used will all be visible.
For me, the cipher used is ECDHE-RSA-AES256-GCM-SHA384.
Because it provides no advantage. TLS is used to secure any data sent to a server. If you don't trust the server with your password, then you should use a unique password for this website. In fact, you should always use a unique password.
https://www.cloudflare.com/en-ca/learning/ssl/transport-layer-security-tls/
Passwords are always sent to the server, then it is hashed to check it against the value in the database. It's also possible to view your password by inspecting login requests from other websites. TLS is used to secure it while in transit.
Hashing is done as an extra measure of security in case the database is compromised. This measure of security would have been completely void if the server would accept password hash directly. You could log in as any user by using his compromised hash.
