
So Mustafa steals from the entire world and justifies it by pointing to an abstraction that cannot be proven. It's already complete as they can admit it now and throw Billions at corrupt judges over a decade which will be too late.
These tech-god pyschopaths hate us.
- Women hide thier skin, lips, and age
- Men hide thier jawline with beards and their insecurities are buried so well, they forget it themselves as a defense mechanism hoping the mental/emotional weakness will "heal" by next confrontation
- Humans hide thier weakness,
- Thier competitive business plans
- Patents until they are published
- Who are you falling in love with at the start
- Exactly how much you are attracted to a person
- Who you have a crush on
- Your answer to a $10,000 competition
- Your lottery ticket
- The location of your gold and gun
- The location of your child when allowed online
- Whether someone is away from home for extended periods of time, you leave the lights and TV on.
- Inventions until it's marketed
- Science Fair Project until it's unvieled
- Presents until they are opened
- Your private parts
- Your private thoughts on your marriage
Have you ever grabbed a childs private parts? NO of course not, because you INNATELY UNDERSTAND even though you are not a parent and don't remember being one yourself. In fact you understand it so well that if you were to do so publcally, you're putting your life at risk.
CONCLUSION: Privacy is natural and helps give confidence and security to an individual but they want access to your weaknesses and privates anyway.
EVIDENCE: Privacy Violation is a specific tactic meant to break people ...IN PRISON..since they begining of time, Gulags.
P.S. Stop showing nude baby pictures at reunions to those that did not raise or grow up with the child in the family who already saw them naked, and only while they are still a child and not a teenager, otherwise that is a serious privacy violation. In fact, just don't take the picture, where did you even get that you lazy lubricated louse.
Very interesting tip, preciate that.
@PassGAN
Instead of relying on manual password analysis, PassGAN uses a Generative Adversarial Network (GAN) to autonomously learn the distribution of real passwords from actual password leaks, and to generate high-quality password guesses. Our experiments show that this approach is very promising.
Masterful wordsmithing, I must find a place for this quote in my future writing. I'll save and credit.
Odd vote rating Lemmy, what gives? I mean, it is kinda of an odd connection, but the Sun affects everything about everything with an effect envelope the size of the Galaxy. It is literally the most powerful thing in our existence and the reason you are alive?
I want to confirm this. Hacker News is nothing like it used to be and is approaching the cliff of "group think" narrator, the opposite of Entrepreneurship.
This gets a vote from me for "Best of the Internet 2024", brilliant pacing, super braced, and with precision bluntness. I'm going to pretend the Monero remark is not even there, that's how good it was.
Thanks for all the comments affirming my hard working planned 6 month AI honeypot endeavouring to be a threat to anything that even remotely has the possibility of becoming anti-human. It was in my capability and interest to do, so I did it. This phase may pass and we won't have to worry, but we aren't there yet, I believe.
I did some more digging in Perplexity on niche security but this is tangential and speculative un-like my previous evidenced analysis, but I do think I'm on to something and maybe others can help me crack it.
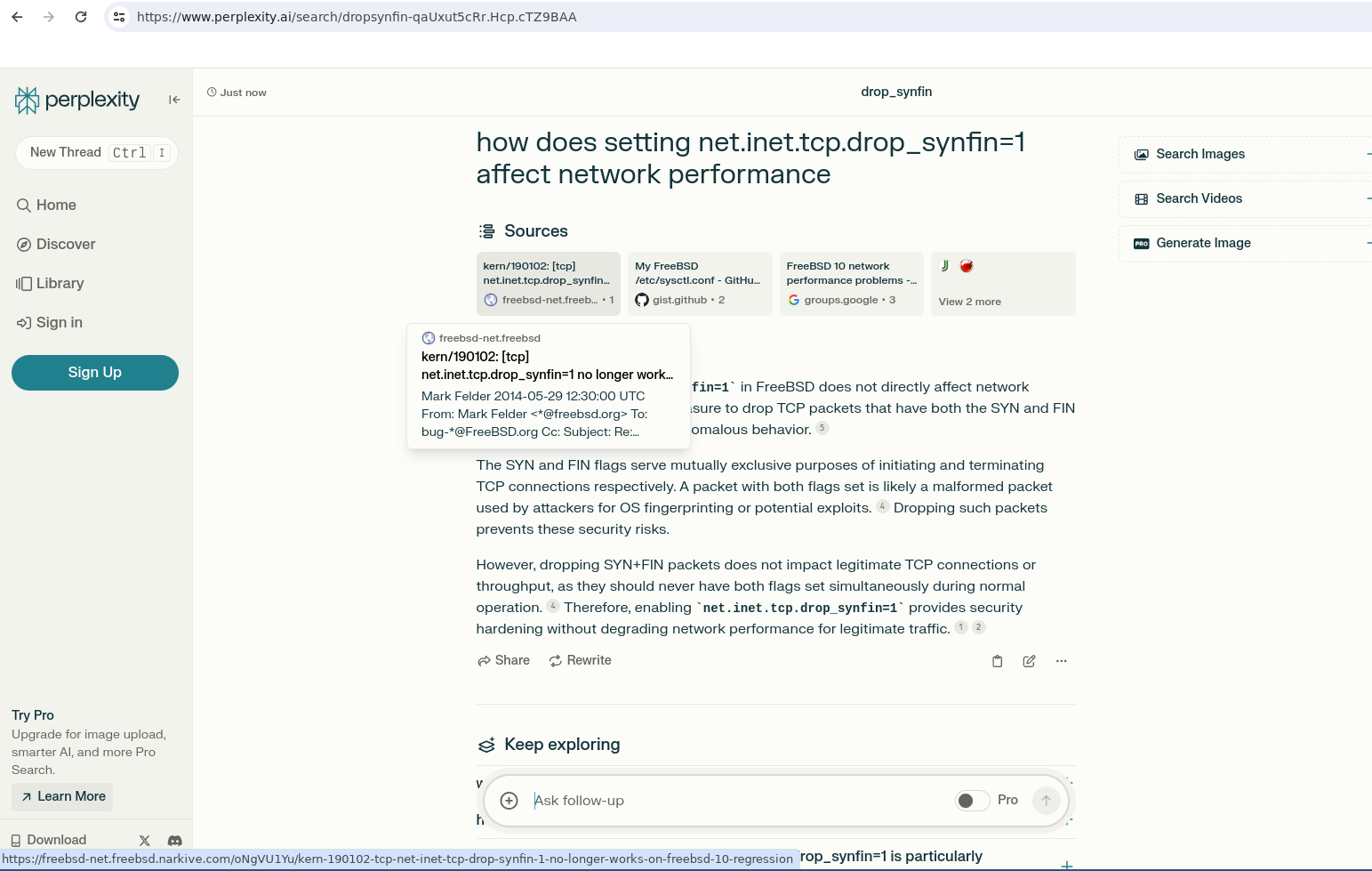
I wrote this nice article https://www.quadhelion.engineering/articles/freebsd-synfin.html about FreeBSD syscontrols tunables, dropping SYN FIN and it's performance impact on webhosting and security, so I searched for that. There are many conf files out there containing this directive and performance in aggregate but I couldn't find any specific data on a controlled test of just that tunable, so I tested it months ago.
Searched for it Perplexity:
- It gave me a contradictorily worded and badly explained answer with the correct conclusion as from two different people
- None of the sources it claimed said anything* about it's performance trade-off
- The answers change daily
- One answer one day gave an identical fork of a gist with the authors name in comments in the second line. I went on GitHub and notified the original author. https://gist.github.com/clemensg/8828061?permalink_comment_id=5090233#gistcomment-5090233 Then I went to go back and take a screenshot I would say, maybe 5-10 minutes later and I could not recreate that gist as a source anymore. I figured it would be consistent so I didn't need to take a screenshot right then!
The forked gist was: https://gist.github.com/gspu/ac748b77fa3c001ef3791478815f7b6a
[Contradiction over time] The impact was none, negligible, trivial, improve
[Errors] Corrected after yesterday, and in following with my comments on the web that it actually improves performance as in my months old article
- It is not minimal -> trivial, it's a huge decision that has definite and measurable impact on todays web stacks. This is an obvious duh moment once you realize you are changing the TCP stacks and that is hardly ever negligible, certainly never none.
drop_synfinis mainly mitigating fingerprinting, not DOS/DDoS, that's a SYN flood it's meaning, but I also tested this in my article!
Anyone feel like an experiment here in this thread and ask ChatGPT the same question for me/us?


Your rapacious backwards insult of caring is gross and obvious. You called me "my dude" like a teenger whose chill, and calm, and correct, but just ...a child and wrong in the end. How old are you child? My Lemmy profile is my name with my Seal naturally born March 4th, 1974 as Elias Christopher Griffin. I've done more in my life than most people do in 10. My mental health is top 3% as is my intellect.
You are an un-named rando lemmy account named "catloaf" who averages 16 posts a day for the past 4 months with no original posts of your own because you aren't original.
I make only original posts. You seem nothing like a real person. Want to tell us who you are? What makes you special, outside of the mandated counseling you recieve or data models you intake?
You know what, no one takes what you say seriously loaf of cat, I certainly didn't, don't, and won't. Here is space for your next hairball
I also just realized why I'm getting heat here, lawsuits.
I just gave legal cause that practice was not properly disclosed by Microsoft, abused by OpenAI, a legal grounds as a README.markdown containg code as being software, not speech, integral to licensed software, which is covered by said license.
If an entity does find out like me your technical writing or code is in AI from a README, they are perhaps liable?
It all started with this today:
Perplexity AI Is Lying about Their User Agent https://rknight.me/blog/perplexity-ai-is-lying-about-its-user-agent/
The comments so far aren't real people posting how they really feel. An agenda or automata. Does that tell you I'm over the target or what?
Look my post is doing really well on the cyberescurity exchanges. So to all real developers and program managers out there:
Recommend the removal of any "primary logic" functional code examples out of your README.md, that's it.
PSA, Here to help, Elias
I write the smartest in the room, passionate, with wisdom and evidence. The way you defame someone like this makes me definitely sure you are not afraid to defame someone's character with no evidence of anything but your own stupidity and un-awareness.
Discussion Primer: From my perspective and potential millions of others, the readme is part of the software, it is delivered with the software whether zip, tar, git. Itself, Markdown is a specifiction and can be consider the document as software.
In fact README is so integral to the software you cannot run the software without it.
Conclusion: I think we all think of readme, especially ones with examples of your code in your readme, as code. I have evidence AI trains on your README even if you tell it specifally not to use readme, block readme, block markdowns, it still goes after it. Kinda scary?
I want everyone else to have the evidence I have, Science.
Sounds like AI or an AI influencer post. The first paragaph is so far off-topic, might as well be talking about sailing. You completely mis-understood what I meant using TabNine. I wrote my own code and obfuscated my own code. Then tried to have AI complete another function using my code.
Nothing you said is relevant is any way, shape, or form.
[EDIT} https://www.tabnine.com/

I used to be the Security Team Lead for Web Applications at one of the largest government data centers in the world but now I do mostly "source available" security mainly focusing on BSD. I'm on GitHub but I run a self-hosted Gogs (which gitea came from) git repo at Quadhelion Engineering Dev.
Well, on that server I tried to deny AI with Suricata, robots.txt, "NO AI" Licenses, Human Intelligence (HI) License links in the software, "NO AI" comments in posts everywhere on the Internet where my software was posted. Here is what I found today after having correlated all my logs of git clones or scrapes and traced them all back to IP/Company/Server.
Formerly having been loathe to even give my thinking pattern to a potential enemy I asked Perplexity AI questions specifically about BSD security, a very niche topic. Although there is a huge data pool here in general over many decades, my type of software is pretty unique, is buried as it does not come up on a GitHub search for BSD Security for two pages which is all most users will click, is very recent comparitively to the "dead pool" of old knowledge, and is fairly well recieved, yet not generally popular so GitHub Traffic Analysis is very useful.
The traceback and AI result analysis shows the following:
- GitHub cloning vs visitor activity in the Traffic tab DOES NOT MATCH any useful pattern for me the Engineer. Likelyhood of AI training rough estimate of my own repositories: 60% of clones are AI/Automata
- GitHub README.md is not licensable material and is a public document able to be trained on no matter what the software license, copyright, statements, or any technical measures used to dissuade/defeat it. a. I'm trying to see if tracking down whether any README.md no matter what the context is trainable; is a solvable engineering project considering my life constraints.
- Plagarisation of technical writing: Probable
- Theft of programming "snippets" or perhaps "single lines of code" and overall logic design pattern for that solution: Probable
- Supremely interesting choice of datasets used vs available, in summary use, but also checking for validation against other software and weighted upon reputation factors with "Coq" like proofing, GitHub "Stars", Employer History?
- Even though I can see my own writing and formatting right out of my README.md the citation was to "Phoronix Forum" but that isn't true. That's like saying your post is "Tick Tock" said. I wrote that, a real flesh and blood human being took comparitvely massive amounts of time to do that. My birthname is there in the post 2 times [EDIT: post signature with my name no longer? Name not in "about" either hmm], in the repo, in the comments, all over the Internet.
[EDIT continued] Did it choose the Phoronix vector to that information because it was less attributable? It found my other repos in other ways. My Phoronix handle is the same name as GitHub username, where my handl is my name, easily inferable in any, as well as a biography link with my fullname in the about.[EDIT cont end]
You should test this out for yourself as I'm not going to take days or a week making a great presentation of a technical case. Check your own niche code, a specific code question of application, or make a mock repo with super niche stuff with lots of code in the README.md and then check it against AI every day until you see it.
P.S. I pulled up TabNine and tried to write Ruby so complicated and magically mashed, AI could offer me nothing, just as an AI obsucation/smartness test. You should try something similar to see what results you get.
So this is the second mention of a rubber duck. I'm trying to fiercely convince myself that talking to a toy on your desk was absolutely not a real thing for adults and that this is some satire I'm missing.
If it's true, that's beyond shameful for an adult. I would quit if I were next to that person's office/cubicle so that they didn't infect me.
In fact, if this was a real thing, don't even tell me. I don't want to live with that kinda shame for my species.
OH, it was been a long time coming seeing this type of headline again, it's....glorius!
Microsoft is most years a #1 and sometimes a #2 Funder of: Rust, Python, and Linux. Are those destined for an E^3 "rug pull" too? Will it ever stop this kind of behavior, consistently conforming our behavior to itself with the money and industry position it leverages?
Don't forget in calculating that industry position that OpenAI is now able to contract to the DoD for offensive capability.
The name sounds akin to "mass gaslighting"?
12 upvotes, twelve, a 6:1 ratio, for "sticking up for Canva" from GHOSTai Media
@Ghostalmedia
I’m from space!
359 Posts 3.94K Comments
Absurd bot numbers. Please don't anyone thinks the above is a real person with a real opinion, I certainly don't. You ("They" when I'm talking to the aware reader of this post) are a paid influencer, bot, AI, group account, etc. The internet is dead because of insanely stupid posts and accounts like this one. Every real designer I know would not touch Canva with a 10ft pole and the Affinity buyout stinks.
Go back to space!

I revised the title many times. Am I giving the impact breadth of what it could be without veering into click-bait?
Bluetooth Low Energy MESH Network, it is built into the OS without any noted country exemption. Although there be will many air gaps, that is not what I mean.
https://www.apple.com/newsroom/2024/05/apple-and-google-deliver-support-for-unwanted-tracking-alerts-in-ios-and-android/
Some questions that came to mind reading it?
- Can China even pull it out of the OS for good measure, hack it?
- Even with topology of some enable, others disable, others wanting security will be reading bluetooth MAC addresses of un-consenting, disabled, for tracking of others whom have enabled, even if they are not being targeted. See below screenshots from the Internet Engineering Task Force presentation.
- Is the Bluetooth freqz and combinatory fields bio-active in any regard of it's function? Do plants stay healthy around "high intake" Bluetooth whatever that may be?
- They mentioned other devices and Industry being involved, how many devices to we expect to also use this protocol in the future?
- If we mapped it out, all of these devices thus operating, mapped out of the whole network with a Supercomputer, real-time, how much energy do you think it would be? How many BLE pulses per second, in a busy metropolitan area?
- Who pushed for this TRACKING NETWORK I will be partcipating in whether I like or NOT (uptake)?
- Where was the pre-planning market and socio-economic research on this presented beforehand?
- If entities very intent on tracking you, will just disable/refuse the protcol, then why instead would Apple and Alphabet whom introduced the vulnerability, just ...make thier own implementation secure?
So we're going to skip this useless marketing-speak on 9to5 Mac - Here’s how the new Cross-Platform Tracking Detection works in iOS 17.5
As far as I can tell, there is nothing that says it doesn't perform assessment of the MAC address in range, all of them, for "your" security of course. In fact, it seems in line with what they want to accomplish: Track all the trackers? Later safeguard them with a "Safefilter" online database check when Phone starts?
Did I get it wrong?
I was a big Markdown fan. I think what finally broke me out was list formatting of mixed types, differences in formats across my repo servers, TOC generation software I was using broke, and no good editors suitable for my tastes for asciidoc that are available on BSD or Alpine Linux.
However, I found out that gedit natively supports adoc and even colors the admonitions. Excellent!
All the guides seem to be too skimpy, not robust enough, or out of order. I like to create as I read.
- Comes with the adoc used to generate the guide and a PDF version.
- Recommends editors with native asiidoc support.
- Gives a comprehensive header "template".
- Enables experimental features, admonition icons, and code highlighting.
- Shows the best read/write table syntax missing from the official guide.
- Corrects two errors in the official guide.
Did you know Asciidoc has a counter increment function?
Although it gives a warning saying not to use if possible, I found it works well for simple tasks.
Enjoy.
https://www.quadhelion.engineering/guides/AsciiDocCheatSheet.html

Science is what is, which requires nor benefits from belief. Adding a belief layer is interpreting, exploitable, and leads to believing untrue things as true (Science).
Reduced Logical Form: I believe what is (true) = Oxymoron
Oxymoron: A rhetorical figure in which incongruous or contradictory terms are combined
Explainer: It is impossible to believe what is true.
---
---Highly Related---
---
Question: 1 - Is it true or false?
Hint: Is/must/can the number/digit/integer 1 (one) be boolean in [all] cases? What are the conditions in which 1 is false?
Test from OCaml:
if 1 then true else false;;
Theorem Pseudocode: if (1 = true) && (2 = 1 + 1) && (2 = true && true) then [true +& true +& ...] = true else nothing else matters
Note my recursive application to all other numbers/physics and inference that if 1 is not true, nothing is true
Postulation: All positive integers are true

This post with embedded music/videos in one blog page
Groking
White Hat
Frida - I Know There's Something Going On, Bladerunner Mix https://soundcloud.com/thebladerunners/frida-i-know-theres-something
Black Hat
VLF Electro https://soundcloud.com/microdosepromotions/sets/wook-chamers
Gray Hat
Dark + Light Electro https://soundcloud.com/xenondream/do-it-to-it-xenondreamix
Battle
CISA NCISS CODE BLACK – 12 minutes until people die https://soundcloud.com/lil-chromosome-unofficial/andrew-hulshult-davoth-doom-eternal-the-ancient-gods-part-2-extended-gamerip
CISA NCISS CODE RED - 11 minutes, 11 seconds until people lose it https://www.youtube.com/watch?v=vwUejFGol9E
Aftermath
A. Against all odds, you WON in near perfection, and you knew you would; Let us bask in your glow. https://www.youtube.com/watch?v=lEr8Gfa-hsk
B. Against all odds, you WON utilizing any/all available means, and it was chaos the entire time; Let us be in awe of you. https://www.youtube.com/watch?v=_PlSTjgcpa8
Apologies for music that could only be found on YT
✳️ Add your music+-scenario! ✳️

Related:
Major cyber attack could cost the world $3.5 trillion - Power Grid, Internet Outage
The one database/file/zip to save humanity, what is it?
Show Lemmy the downloadable URL of a Database or AI you know of so we can have a local backup copy that will improve the resilience and availability of Human Knowledge.
Given the state of AI being Corporatized I think we could definitely use links for whatever comes closest to a fully usable Open Source, fully self-contained downloadable AI.
Starter Pack:
- Wikipedia Single 100GB File
- http://sci-hub.wf/
- Arxiv Download Script
- https://wholeearth.info/
- https://the-eye.eu/
- Endless OS "Offline Library"
- scikit-learn AI with External Databases
- ScienceFair
★ Lemmy List
Databases
AI

I'm personally motivated in a non-commercial way to supply everyone with as much cybersecurity as possible in the interests of civlization, especially now. I've just finished what I wanted to releae as "set" 2 days ago and it's time to announce them.
I'm the former Web Application Security Team Lead for the National Computer Center, Research Triangle Park, having been contracted to the EPA by the now defunct Computer Sciences Corporation.
If you have some extra hardware not really being used I would suggest perhaps a great use of it would be to create yourself a hardened platform, just in case, to protect your sensitive data on an emminently stable platform going forward.
Maybe you've always wanted to try a BSD, well now is a great time to do that. They are super stable, super reliable, community drive, and you are in control of everything.
I would also like to mention that if you'd like to go extra hard consider Hardened BSD. Another alternative is using grsecurity/PaX kernel patched Alpine Linux as a Desktop choosing crypt full disk encryption during setup + AppArmor.
Just as an example you can get your hands on a $250 Thinkpad T495 and installing GhostBSD on it is as simple to setup as Linux Mint and runs as fast as a brand new 2023 Windows laptop. If you choose Dragonfly BSD, the fastest BSD, on a T495 (the lastest year fully BSD compatible laptop), my repo will completely configure it for you, complete with all applications needed for a professional developer.
In addition to that I've created a Network Based Firefox hardening solution that wipes the extremely profitable, For-Profit, Mozilla Corporation off your Internet and easily combines with Arkenfox. It removes Mozilla servers from being contacted by any application or service on your machine and does not interfere with web page rendering.
I've created my own Git Repository using Gogs (which Gitea is based on) where you can get all the goods here:
Latest Software
https://quadhelion.dev
Main Website
https://www.quadhelion.engineering
About
https://www.quadhelion.engineering/about.html
Backup GitHub
https://github.com/wravoc
Backup BitBucket
https://bitbucket.org/quadhelion-engineering/workspace/repositories/

Hello everyone!
Former Security Team Lead at the National Computer Center here. I'm a Security Professional with decades of experience in most Operating Systems and Web Applications.
Recently I've gotten weary of the Global Mega-Corp $100 Billion Linux Eco-System, which still manages to provide an unstable OS experience. I've turned my attention to the rock solid and predictable BSD/Unix world whenever I can use them.
I've created security hardending scripts for most BSDs except for NetBSD which is next in line. What would normally take an experienced SysAdmin an hour to complete, covering kernel mitigations, file system permission, daemon permissions, password encryption, etc can be done in seonds by a new user, with conf file verifications, backups, logging, and pretty printing the output to console.
- FreeBSD
- GhostBSD
- DragonflyBSD
- OpenBSD
For Dragonfly BSD, the fastest BSD, with a filesystem in the news lately that recovers itself and provides automatic snapshots down to the file level, I went ever further and created a rice for it using AwesomeWM. You are in luck if you have a Thinkpad T495 because I also wrote a full installation script for it for DF!
In addition to that I did it right and got explicit permission for Logo use or attained sponsorship and included the Wallpaper+Icon pack you see above.
You grab it all for my free on my self-hosted git repo for free at: https://quadhelion.dev/
Although I use a custom License which is somewhere between copyleft and copyright, it is generous enough to allow you to accomplish whatever task you wish and provide protections for my work and future oppourtunities for me.
I'm not liking the direction GitHub is going but you can find my work there: https://github.com/wravoc
I hope you find it useful and you are free to ping me here or write to my email listed on the main website page with any concerns.
Thanks,
- Elias
- @wravoc
- @erogravity
 Elias Griffin @lemmy.world
Elias Griffin @lemmy.world Desert Nomad, First Responder, Reverend, Intelligence Analyst, Computer Expert, Cowboy, Sorcerer, Metaphysician, Polymath.
- https://bio.site/ecg